BlackBerry’s cybersecurity division has identified malware families and tools most prevalent in cryptojacking breaches between March and May.
Cryptojackers, believed to be Russian, attacked Linux-based systems with the open-source tool XMRig and the Prometei botnet.
BlackBerry Highlights Growing Arsenal of Malware Tools
According to BlackBerry, hackers initially unleashed Prometei to Linux-based VMWare ESXi servers in all countries except Russia, Ukraine, Belarus, and Kazakhstan. Later attacks excluded only Russian systems.
Around since at least 2020, Prometei piggybacks off different internet domains, making it difficult to trace and stop. Additionally, the botnet runs on Windows machines.
Hackers used Prometei to mine cryptocurrencies like Monero.
BlackBerry’s team also found that SmokeLoader, categorized as a ‘dropper’ in cybersecurity parlance, is a tool criminals favor to load malware. Distributed through spam and various phishing attacks, SmokeLoader survives reboots and hides itself in legitimate computer operations.
After installation, it can download and load more malware and frustrate quarantine attempts.
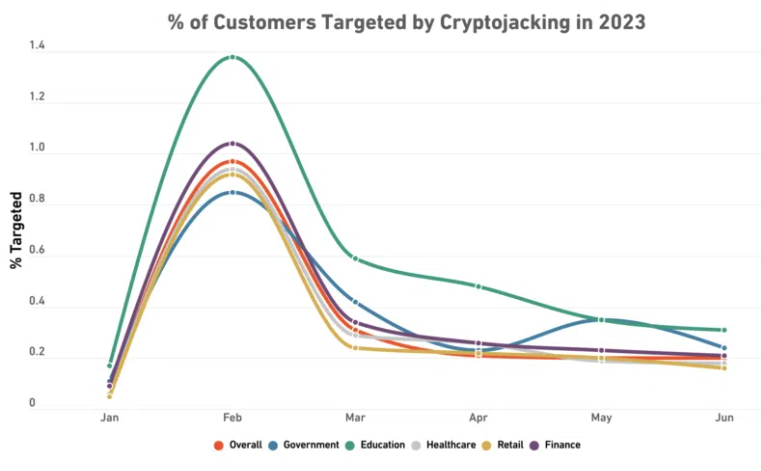
Cybersecurity firm SonicWall recently reported that cryptojacking incidents rose 399%year-on-year by the end of June. Hackers targeted the Oracle cloud and also breached macOS devices through HonkBox cryptojacking malware embedded in cracked applications.
Go to Source to See Full Article
Author: David Thomas






