About two-thirds of crypto incidents investigated by blockchain analytics company AMLBot in 2025 were driven by social engineering rather than technical exploits, according to a report based on the company’s internal casework.
AMLBot said 65% of the incidents it reviewed last year involved access and response failures, such as compromised devices, weak verification and delayed detection, instead of vulnerabilities in blockchains or smart contracts.
The company said its analysis drew on about 2,500 internal investigations and should not be read as an industry-wide measure of crypto crime, according to a Wednesday report shared with Cointelegraph.
Primary attack vectors included device compromises via chat scams, impersonation scams, and other investment and phishing scams involving social manipulation.
Crypto phishing attacks are social engineering schemes that don’t require hacking code. Instead, attackers share fraudulent links to steal victims’ sensitive information, such as the private keys to crypto wallets.
The findings suggest that security improvements at the protocol level may not be enough to protect users if scammers can bypass safeguards by targeting people directly.
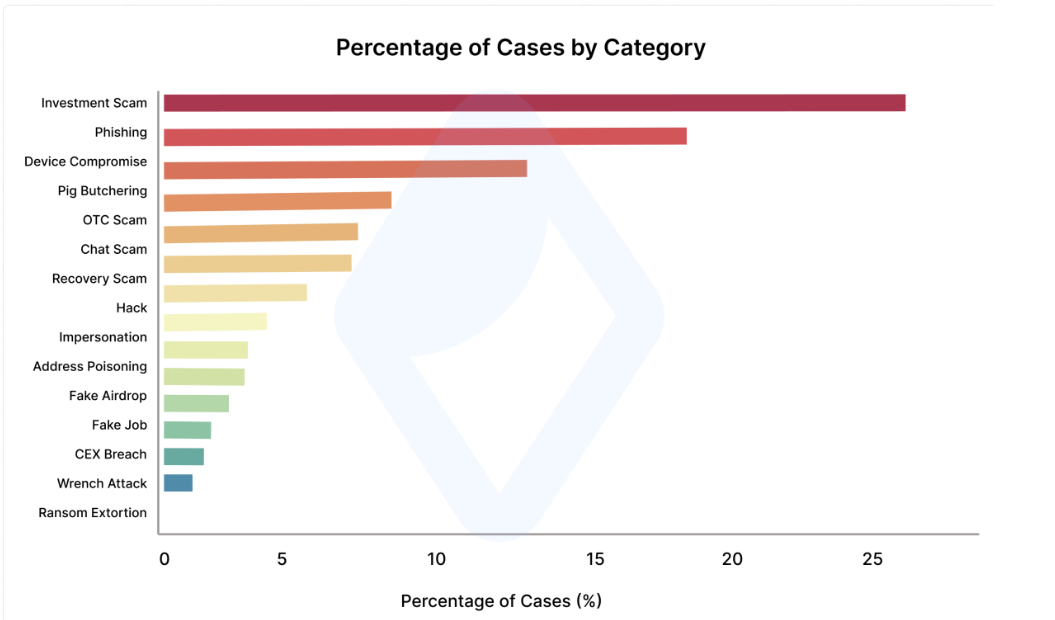
Investment scams and phishing lead by case count
Investment scams accounted for the largest share of cases (25%), followed by phishing attacks (18%) and device compromises (13%), as the most damaging categories in terms of case frequency.
Related: 22 Bitcoin worth $1.5M vanish from Seoul police custody
Pig-butchering scams accounted for 8%, over-the-counter (OTC) fraud for 8%, and chat-based impersonation represented 7%, collectively making up the second tier of the most frequent attacks.
Impersonation linked to $9 million in recent losses
AMLBot traced at least $9 million in stolen digital assets to impersonation-related attacks over the past three months.
Impersonation is the most damaging attack vector in terms of social engineering scams, Slava Demchuk, CEO of AMLBot, told Cointelegraph. “Attackers continue to exploit and trick victims with a ruthless game of charades, posing as trusted entities,” he said. “Sometimes they’re exchange support teams, investment partners, project managers or reps.”
Demchuk urged users not to share private keys or recovery phrases and to be wary of urgent requests involving fund transfers or wallet access, which he said are common entry points for social engineering scams.
Related: Binance confirms employee targeted as three arrested in France break-in
To protect against impersonation attacks, Demchuk urged crypto investors not to share their private keys and recovery phrases.
He also advised investors to ignore “urgent requests involving fund transfers of wallet access,” which are usually the first point of contact for social engineering scams.
CertiK reports January spike in crypto losses
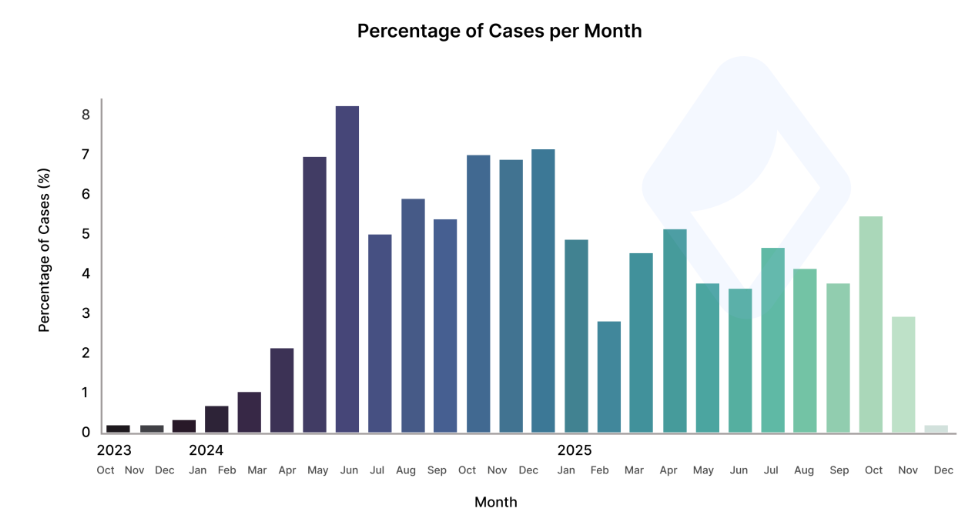
Crypto scams saw an uptick in January, when scammers stole $370 million, the highest monthly figure in 11 months, according to crypto security company CertiK.
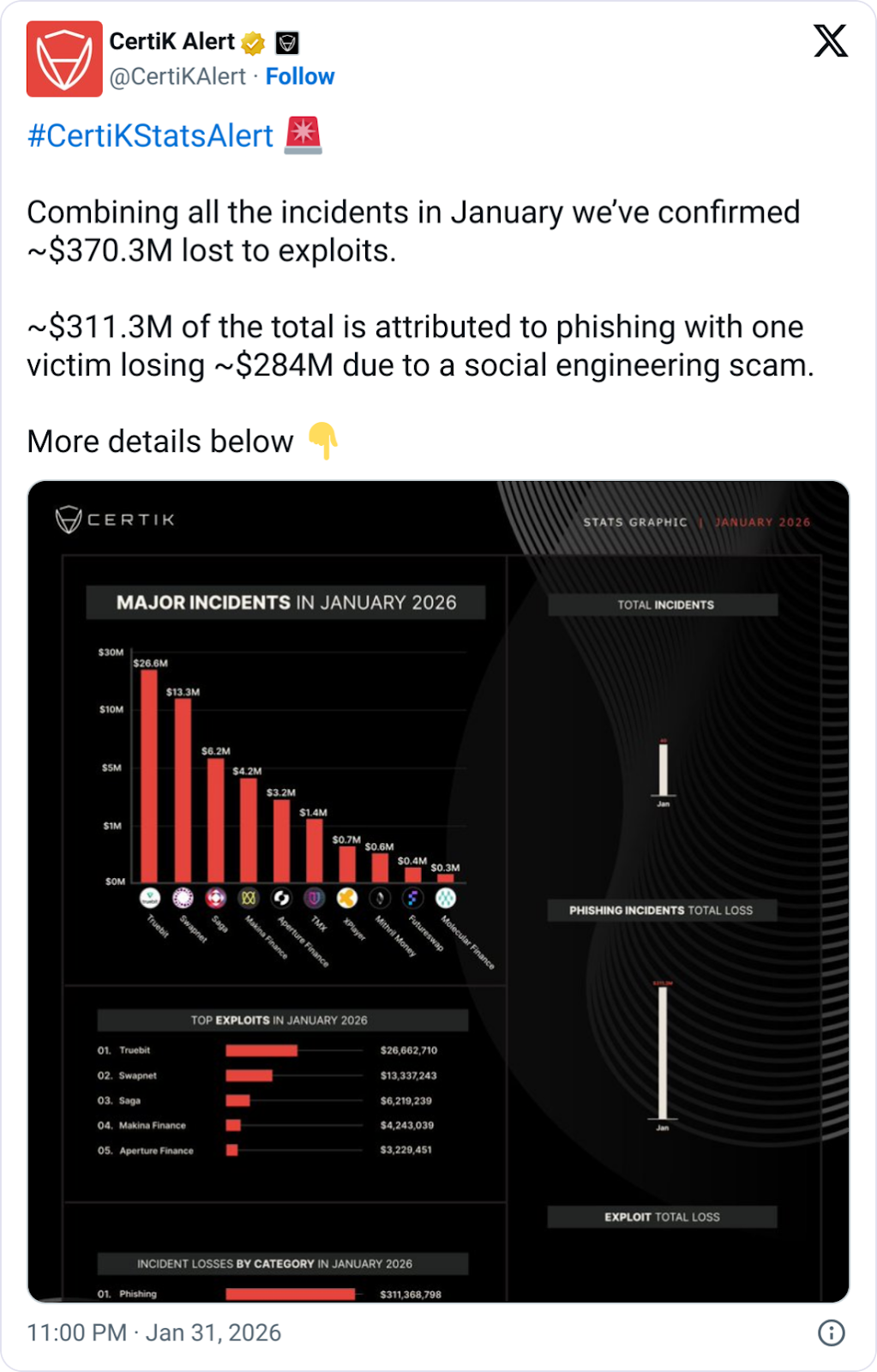
$311 million of the total value was attributed to phishing scams, with a particularly damaging social engineering scam costing one victim around $284 million.
Magazine: Meet the onchain crypto detectives fighting crime better than the cops
Go to Source to See Full Article
Author: Zoltan Vardai